Hacking Windows Domains: Introduction
 |
| Part 1 of the Active Directory series. |
Wilkommen, everyone! After a few hurdles with my homelab server throwing a fit and forcing me to frantically recover my VM's so I could get all of my files off of my file server and temporarily into the cloud, I'm back with a new setup. I've moved from Hyper-V to ESXi, which I always liked for the ease of the web interface, and I've finally been able to recreate my hacking lab as well as my Kali machine that I use to learn on.
As I work towards a pen test certification, I've been using a handful of resources to learn and get hands-on time. First up has been the great Active Directory rooms at Try Hack Me. The other has been the great Complete Practical Ethical Hacking course from TCM. This lab will be setup similar to the lab in the PEH course, as it makes it a bit easier to follow along with Heath's videos. There's always Hack the Box to get some hands on time as well, but that's something better saved for another post.
Now on to the lab we'll be working in while learning to enumerate and sneak around in a Windows domain. Welcome to the humble Test Lab Org. This is a small business with only 3 employees. There's the owner, Diana, her Husband Dave, and lastly the de-facto IT person and grunt employee, Bob. They are a small shop that currently find themselves flooded with new business, which means a lot of corners have been cut to get things working. Bob took a class on computers once in school, which was enough for his parents to decide he was ready to take the crown of "Director of IT". Unfortunately for Bob, he slept through the majority of that class, meaning he just pretty much knows where to plug things in. Fortunately, he's got Google, so he's been able to find his way around and make things work.
Their network is small, with only 3 desktop computers running Windows 10 and a Domain Controller running Server 2019. While Googling around, Bob found out that a Domain Controller would make things easier, and allow him to setup accounts for everyone. While the company is rolling in business, they aren't exactly flush with cash. Wanting to make the most out of what he had, and to get his mother off his back, Bob has setup the domain controller as a file server so everyone can share their files. This is what the network looks like:
- TestLab-DC-01 (192.168.2.1): Bob set this machine up to hopefully make his life a little easier. Their ISP-provided router wasn't working well, so with the help of Google, Bob has managed to configure the Domain Controller as a DNS/DHCP device to help limit the number of times his Dad yells out of his office about the "internet being broken". He also setup a file share so that everyone can access their files all the time, since his parents kept saving things to their desktops and saving separate copies of everything.
- TestLab-HR-01 (192.168.2.101): Being the forward thinking person he is, Bob setup his Mom's computer as the HR computer as well, figuring it would come in handy someday when the company expanded. After a few weeks of his Mom yelling that she couldn't "install anything" he just made her a local admin and also added himself so he could make changes whenever he needed to.
- TestLab-IT-01 (192.168.2.102): Bob's own computer has a file share on it that he uses to place his own IT files for installs on his parents' computers, as leaving them in the file share meant his Mom and Dad would constantly delete them on accident.
- TestLab-FD-01 (192.168.2.103): Dave, wanting to be the face of the company, had his son place his computer at the Front Desk. Similar to his Mom's computer, Bob went ahead and added his Dad as a local administrator and added himself as an administrator to let him install and work on things after hour without anyone hovering over his shoulder.
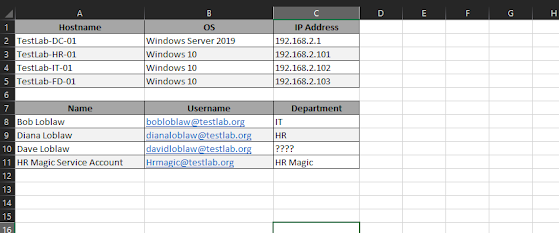 | ||||
- Bob Loblaw (bobloblaw@testlab.org): Bob's got his own account setup to maximize his time. He made himself Domain Admin on all of the machines so that he wouldn't run into any permission issues trying to make changes or install anything.
- Diana Loblaw (dianaloblaw@testlab.org): Bob mentions that he made his Mom's account a local admin on her machine, because she kept getting mad that things wouldn't work right for her. Adding her account as local admin on TestLab-HR-01 seemed to sort the issues out for her, and he's been complaint free ever since.
- Dave Loblaw (davidloblaw@testlab.org): Bob mentioned that he similarly setup his Dad's account as local admin on his machine.
- HR Magic (HRmagic@testlab.org): Bob mentioned that they use some software called HR Magic that they use to process the HR data for their customers. Bob said he didn't really understand what they did as a company, since that was "above his pay-grade", but he knew that it was important that the account be able to get to the SQL database without any issues.
So where do we come in? Well, we've been asked to lend a hand. Not having a lot of money to spare, Bob has enlisted us to help him check their company for any glaring security issues that might open them up to potential trouble. We'll explore the various ways we are able to scan the network to find machines and users, and then expand on that to find the ways we can potentially exploit things, all with the end goal of helping Bob secure their network and keep everyone's information safe.
Keep an eye out for part 2, coming later next week!
Comments
Post a Comment